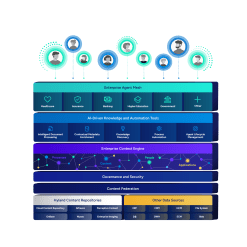
OnBase
Intuitive, flexible, powerful low-code solutions
“Incredible suite of tools for managing complex processes, ensuring stability and audit trails, rapid app development, and pretty much any crazy requests our users and business owners propose for us. Easily my favorite system to work in and support.”